Aria Operations for Logs #10 vCenter-ESXi Anomaly Detection
In this article, I will explain how to create a dashboard for anomaly detection in some commands that can be considered potentially dangerous from ESXi logs. You can find anomaly dashboards related to topics such as VM Process, System Permissions, Software VIB, executed python scripts below. In the previous article, you can access the article where we filtered sample ESXCLI commands and created dashboards below.
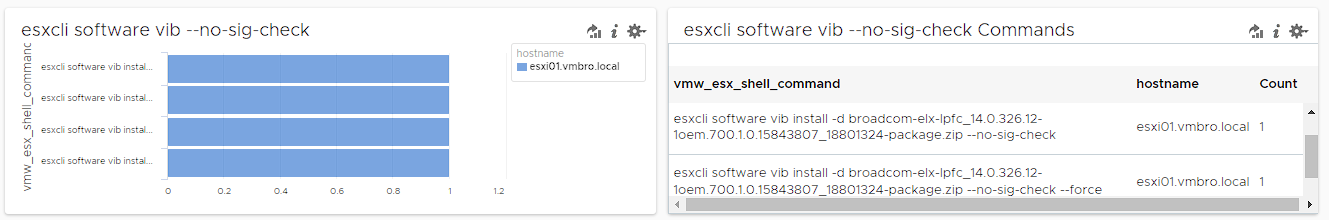
esxcli software vib * –no-sig-check
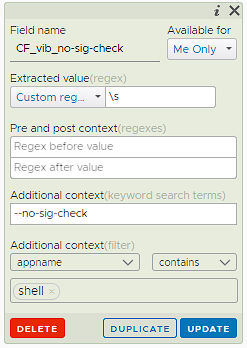
The command executed with -no-sig-check parameter can cause serious security risks as it will bypass acceptance level and VIB signature verifications and disable security measures. First of all, let's duplicate any field with the Manage Fields option on the right side of the screen in the Explore Logs menu.
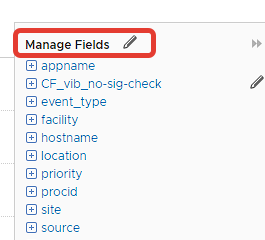
Afterwards, let's create the custom field name CF_vib_no-sig-check, Additional context as -no-sig-check and context filter appname to search shell logs.
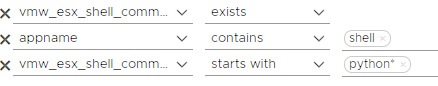
After selecting this field, which we created as a filter as below, as exists, we list the shell logs containing -no-sig-check.

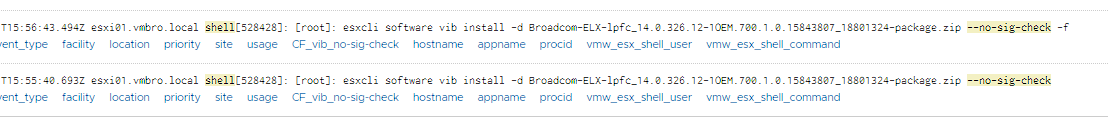
Then you can group your query by hostname and vmw_esx_shell_command and visualise it with table or bar view.
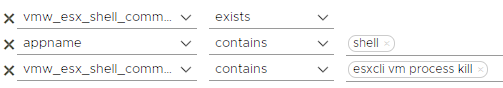
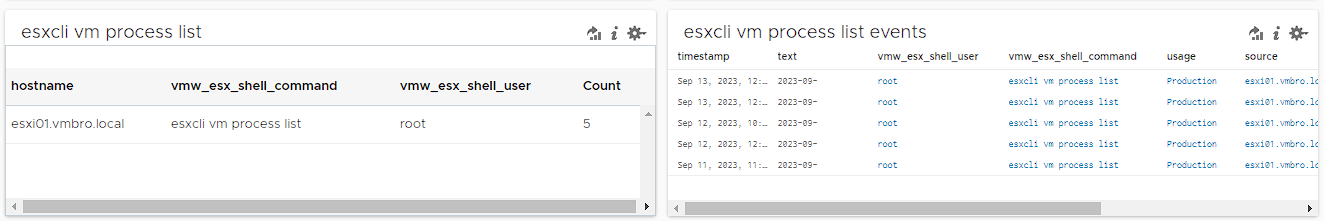
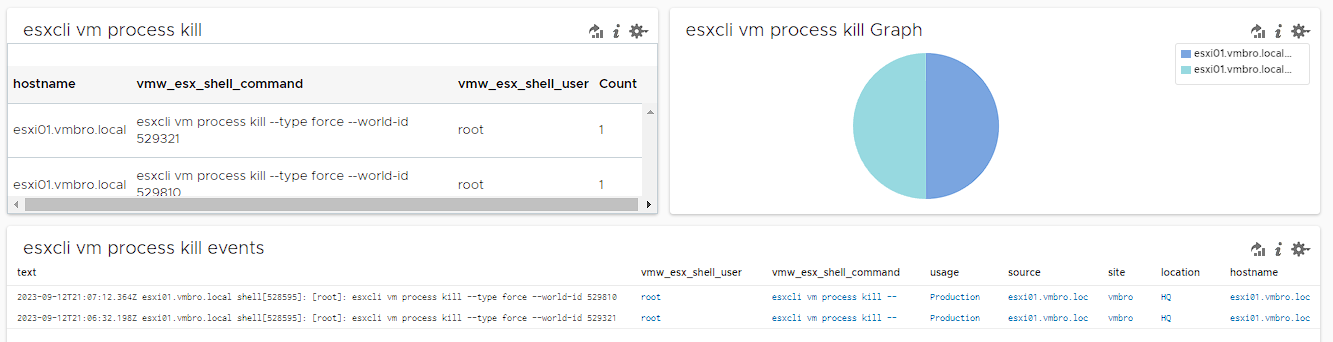
esxcli vm process list / esxcli vm process kill
According to the reports written for ransomware attacks related to this situation, it has a behaviour such as listing and terminating virtual machines on the host. You can use the filters below to detect anomalies in these activities.
ESXi executed python script
Detecting malicious scripts running on ESXi host is very important for system security and prevention of malicious activities. Here we will list the python files executed on the ESXi host. These contents that are executed outside of your planned work should be checked.

ESXi PowerCLI Logged in sessions
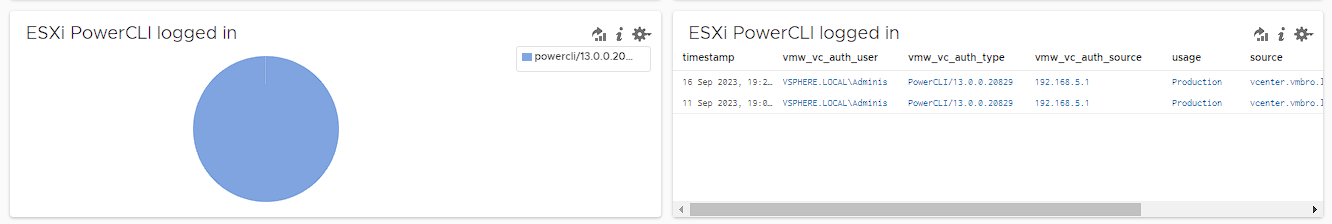
In this section, we will list the sessions that are successfully logged into vCenter with PowerCLI. It is necessary to check who these sessions belong to periodically.
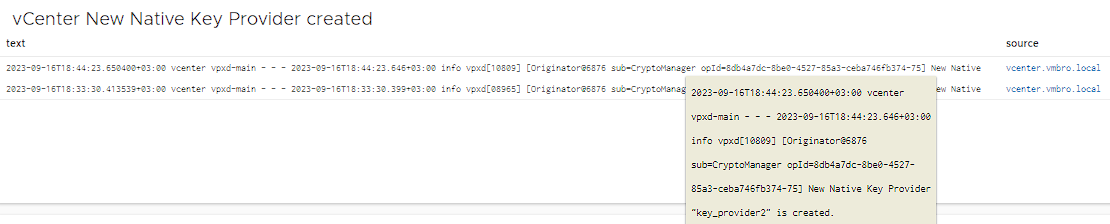
vCenter New Native Key Provider created
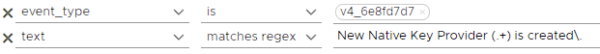
If you are not using encryption methods in your environment, it is useful to monitor the key providers created on vCenter. Below you can find the relevant filter for Native Key Provider. The regex we will use is as follows: New Native Key Provider (.+) is created.
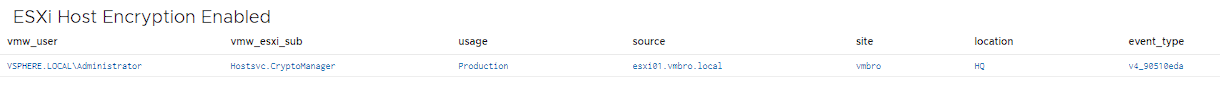
ESXi Host Encryption Enabled
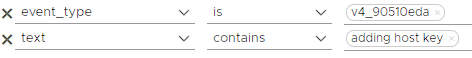
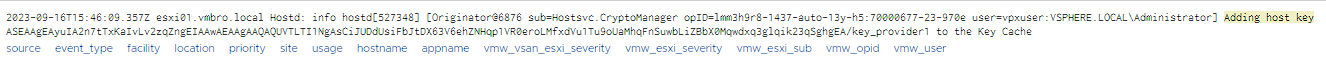
Likewise, if you do not use encryption methods in your environment, we need to know when encryption is activated on your ESXi hosts. For this, it is possible to detect this with the relevant event type and keyword as follows.
esxcli system settings kernel/encryption – execInstalledOnly
By setting execInstalledOnly to TRUE on ESXi hosts with TPM, we can ensure that VMkernel only runs binary files that are packaged and signed as part of a VIB. Disabling the execInstalledOnly advanced parameter can make it more vulnerable to attacks. You can find more information about this topic here


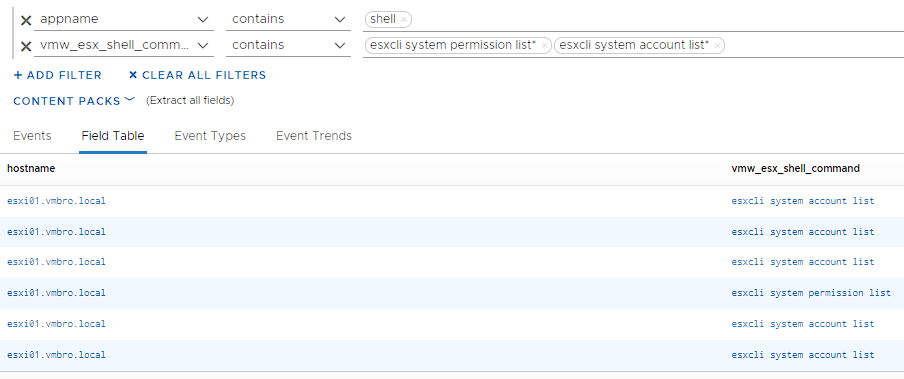
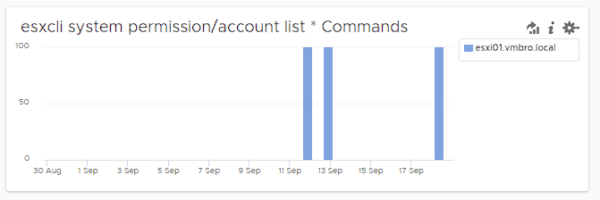
esxcli system permission/account list
A malicious person may try to access information such as access, permissions and accounts on the ESXi host. It may be useful to monitor the listing commands related to user accounts.
esxcli system permission/account commands
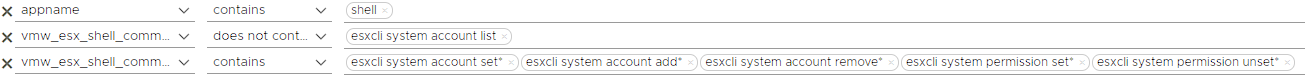
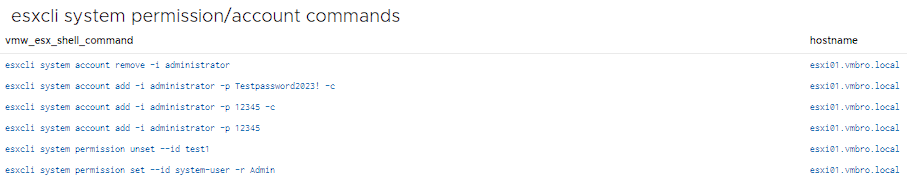
As in the example above, user accounts can use commands such as adding, editing or removing user accounts. It is useful to check such commands separately.
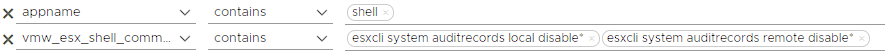
esxcli system auditrecords disable
Here, audit records on ESXi host can be disable with local or remote host options. You can also view this situation with the filter below.
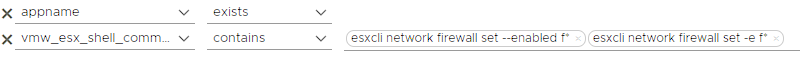
esxcli network firewall disabled
In this section, the firewall on the ESXi host can be disable as in the scenarios above. You can detect firewall disable commands with the following filter.