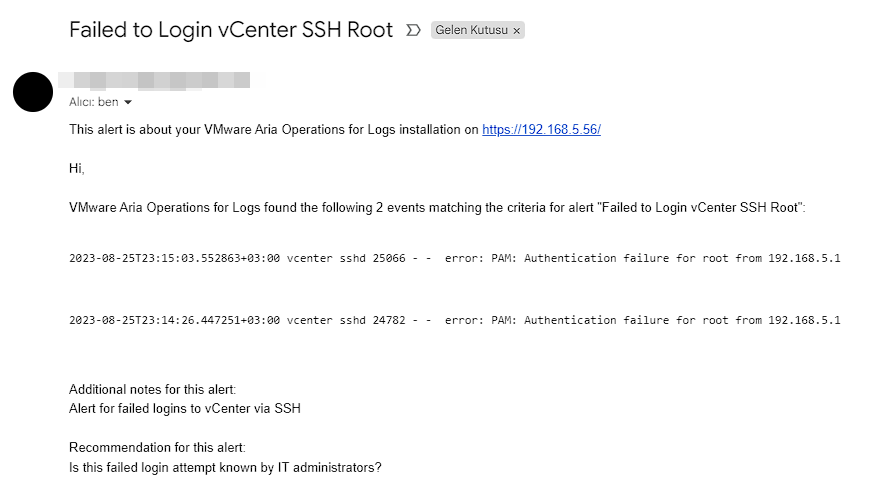
Aria Operations for Logs #2 vCenter SSH Failed Logins
In this article, I will explain how to create alert definitions and dashboards of failed login attempts over SSH with the logs we obtain from vCenter. In my previous article, I talked about the alarms of failed login attempts to the vCenter web interface. If you want to review this article, you can find it below.
Root Account
In this section, I will explain how to list incorrect login attempts with the root account. Since login attempts over SSH with a different user other than root have a different event type, we need to distinguish them. You can find the filters related to the Root account below.
Explore Logs – Query filtering
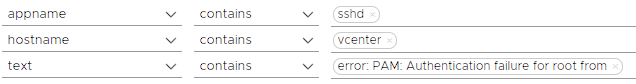
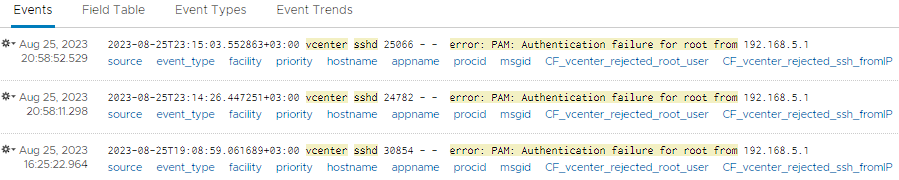
Firstly, in the Explore Logs menu, we will choose the appname value as sshd, hostname value as vcenter and text value as error: PAM: Authentication failure for root from metinlerini içeren log kayıtlarını filtreliyoruz.
Alert Definitions – Creating Alert from Query
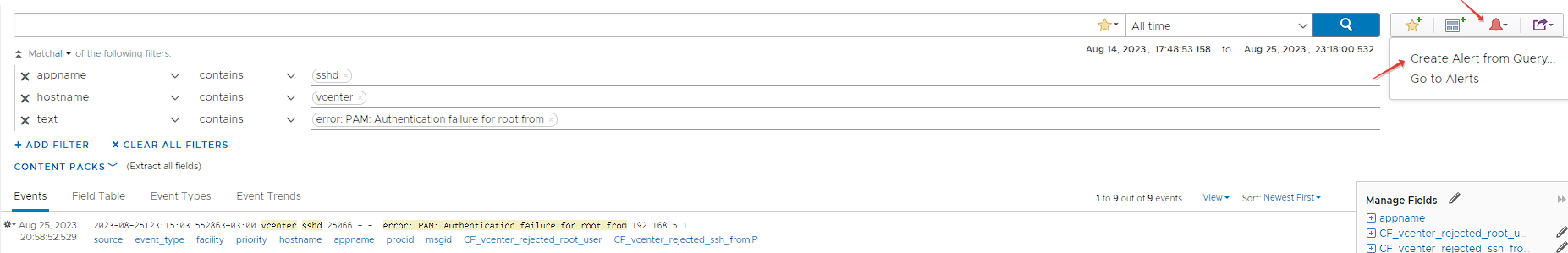
Now let's create an alarm definition for this filter. For this, we press the red alarm button and switch to alarm definition with Create Alert from Query...
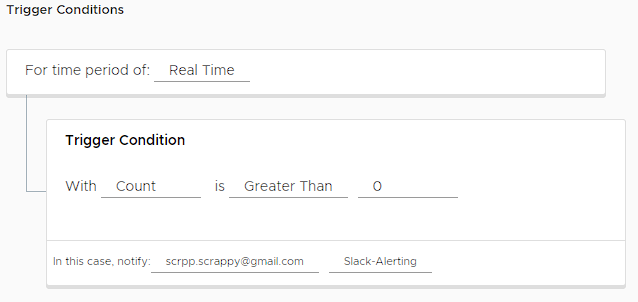
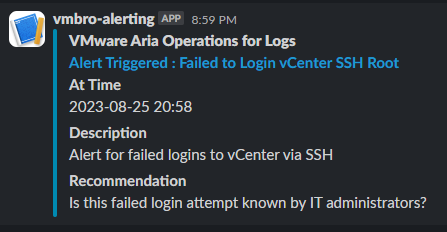
In this section, we fill in the alarm name and description information. Then we select this alarm as Real Time in Trigger Condition. In the current situation, we will receive notification via e-mail and Slack Webhook when the number of events is more than 1.
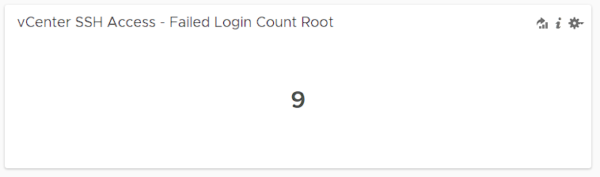
vCenter SSH Access – Failed Login Count
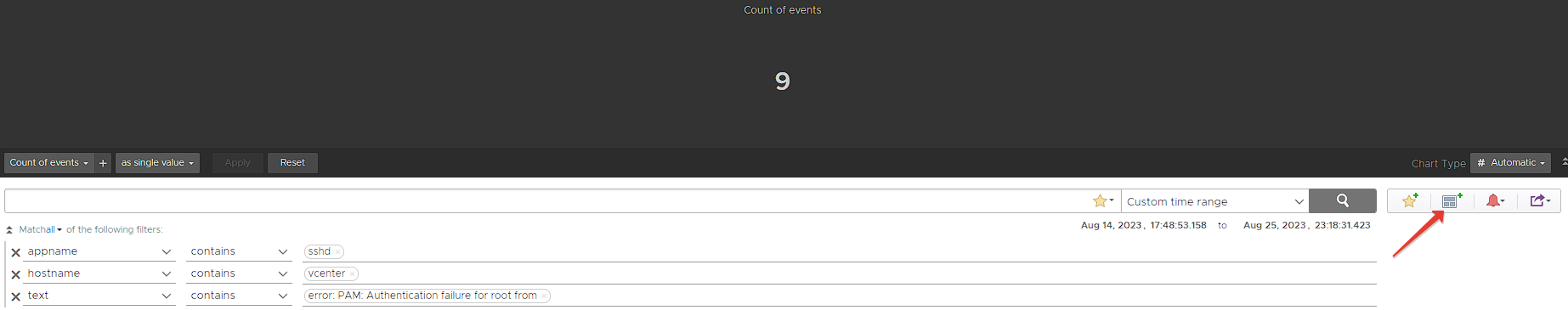
Now, using the same filters that we have defined alarm above, we transfer the total failed entries to a dashboard with the Add query to Dashboard button. Thus, we get an image containing the total number of events as below.
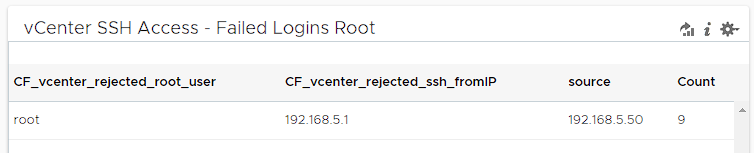
vCenter SSH Access – Failed Logins by Root
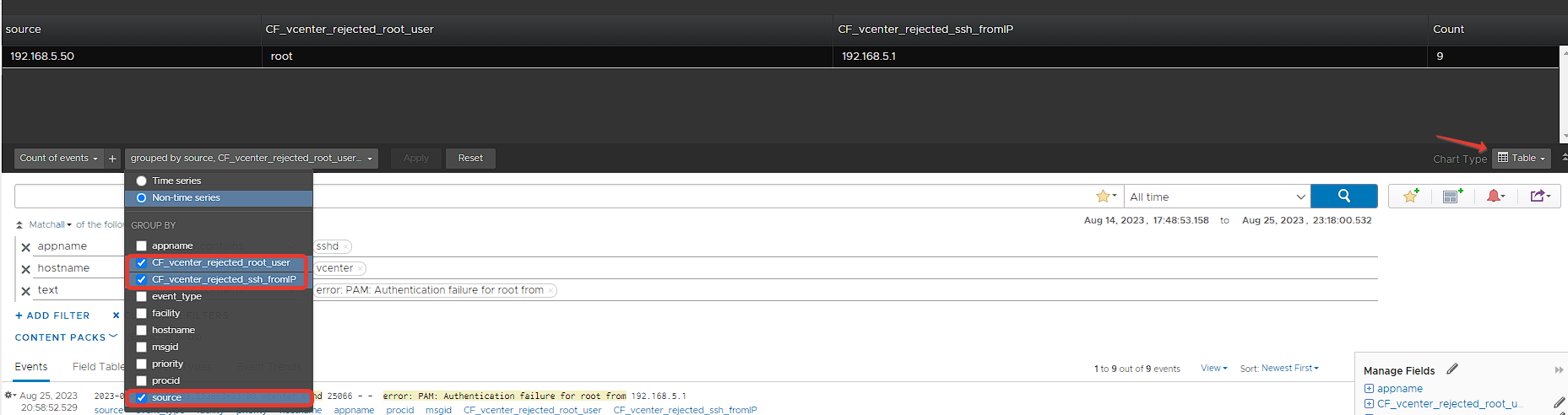
Here, we select the events we obtained with the same filters as non-time series this time and filter them according to Source with Group By. In this way, we will group the failed login attempts to vCenter over SSH according to the Source and transfer them to the dashboard In this way, you can get a view like the one below on your dashboard.
Other User Accounts
In this section, we will filter other user accounts with failed login attempts other than the root account. Then we will prepare dashboards for this alarm condition.
Explore Logs – Query filtering
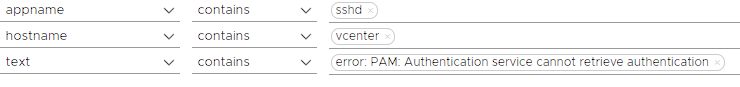
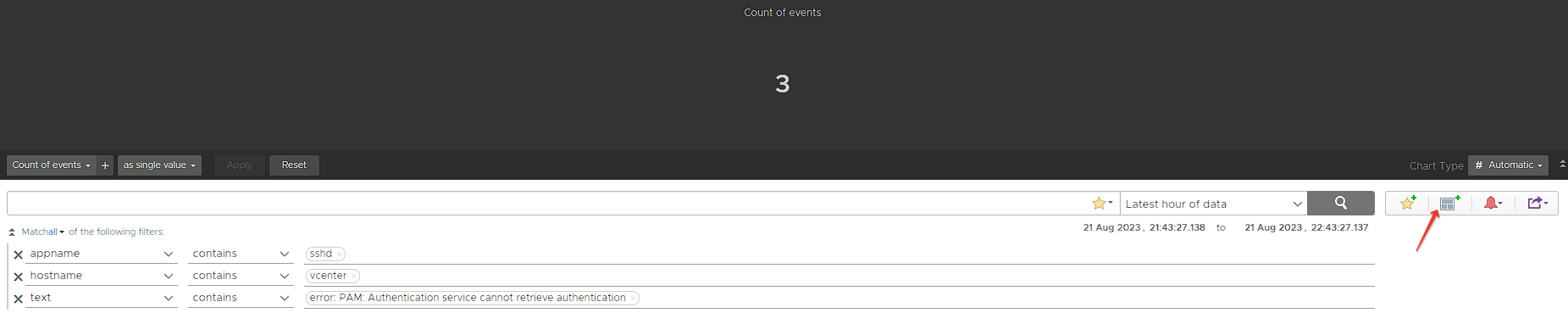
Firstly, in the Explore Logs menu, we will choose the appname value as sshd, hostname value as vcenter and text value as error: PAM: Authentication service cannot retrieve authentication metinlerini içeren log kayıtlarını filtreliyoruz.
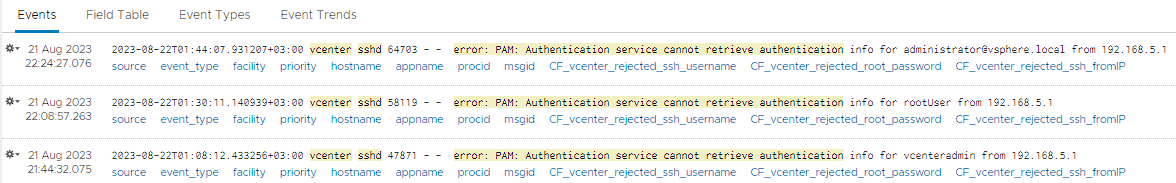
In this way, we can view the log records with failed access over SSH to vCenter.
Alert Definitions – Creating Alert from Query
Now let's create an alarm definition for this filter. For this, we press the red alarm button and switch to alarm definition with Create Alert from Query...
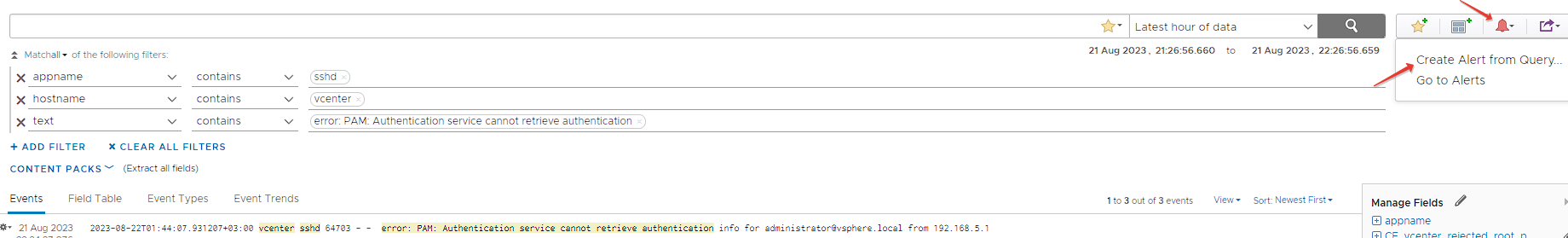
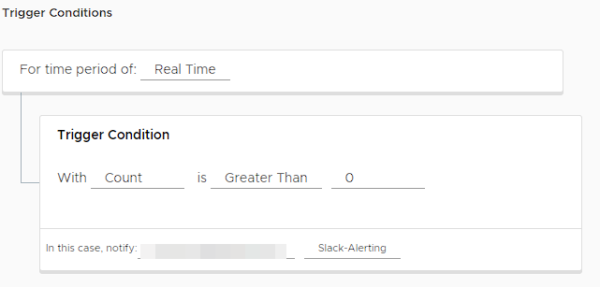
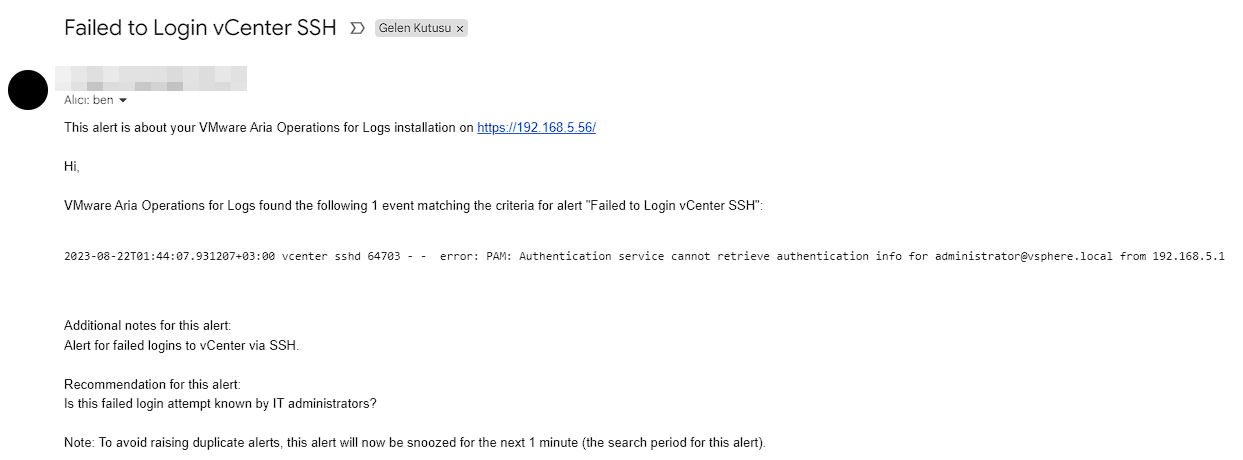
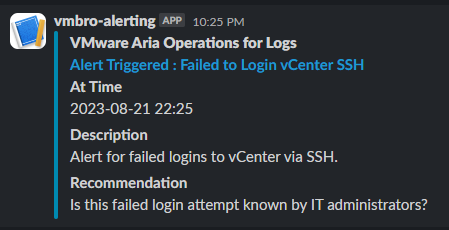
In this section, we fill in the alarm name and description information. Then we select this alarm as Real Time in Trigger Condition. In the current situation, we will receive notification via e-mail and Slack Webhook when the number of events is more than 1.
vCenter SSH Access – Failed Login Count
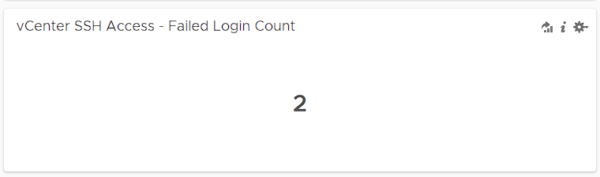
Now, using the same filters that we have defined alarm above, we transfer the total failed entries to a dashboard with the Add query to Dashboard button. Thus, we get an image containing the total number of events as below.
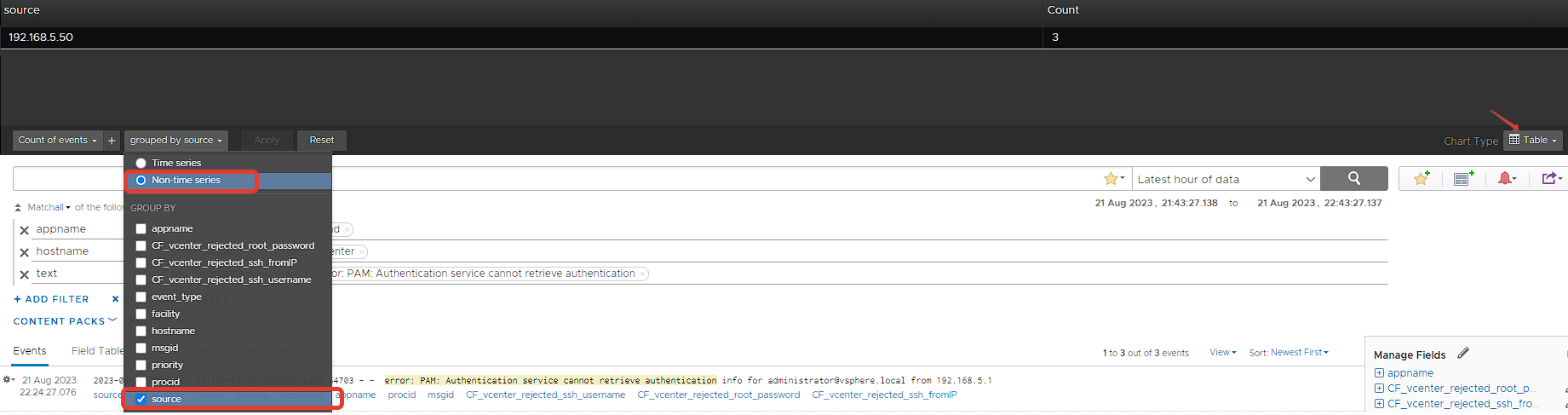
vCenter SSH Access – Failed Logins by Source
As we did in the previous topic, we select these events as non-time series this time with the same filters and filter them according to Source with Group By. In this way, we transfer the incorrect login attempts to vCenter over SSH to the dashboard after grouping Source. In this way, you can get a view like below on your dashboard.

In the continuation of this series, you can reach the next article below, where we create alarms and dashboards of log records with failed login attempts via PowerCLI to vCenter.
